Unified Audit Logging (UAL) in Microsoft 365 is a powerful feature that helps organizations track and retain user and admin activity across services like Exchange Online, SharePoint Online, OneDrive, Teams, and more. Whether you’re investigating security incidents, monitoring user behavior, or ensuring compliance with internal or external regulations, UAL provides a central place to capture it all.
If you’re administering Microsoft 365, enabling UAL is one of the first critical steps toward securing your environment and gaining visibility over activities. In this blog, we’ll walk through what UAL is, why it’s important, and how to enable it.
What is Unified Audit Logging?
Unified Audit Logging consolidates audit records from various Microsoft 365 services into a single, searchable location. It enables administrators, security teams, and compliance officers to search, export, and analyze user and admin activities such as:
- User sign-ins
- File access and sharing
- Mailbox operations
- Admin activities like role changes and configuration updates
- Teams activities like message posts and edits
- Compliance-related events
These logs are accessible through the Microsoft Purview Audit (Standard) or Audit (Premium) solutions, depending on your licensing.
Why is Enabling UAL Important?
Here are several reasons why enabling UAL is crucial for your Microsoft 365 environment:
- Security Investigations: Quickly detect unusual activities like compromised accounts or insider threats.
- Compliance Requirements: Many regulations (like GDPR, HIPAA, and SOX) require detailed activity tracking.
- Operational Insights: Understand how users interact with systems and content.
- Audit Trail: Keep a historical record of changes and accesses for accountability.
- Incident Response: Accelerate root-cause analysis during security incidents.
👉 Without enabling UAL, many audit events simply won’t be logged, leaving blind spots in your monitoring and response capabilities.
How to Enable Unified Audit Logging
Depending on your Microsoft 365 environment, UAL may already be enabled by default. Microsoft started automatically turning it on for tenants in 2019. However, it’s still important to verify.
Step 1: Check if Unified Audit Logging is Enabled
You can check the status by running the following PowerShell command:
- Connect to Exchange Online PowerShell: powershellCopyEdit
Connect-ExchangeOnline - Check UAL Status: powershellCopyEdit
Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabled
If it returns True, UAL is already enabled. If False, you’ll need to enable it manually.
Step 2: Enable Unified Audit Logging (if needed)
If UAL is not enabled, you can turn it on with this command:
powershellCopyEditSet-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
Important: It can take up to 60 minutes for the change to take effect across your Microsoft 365 environment.
Step 3: Verify and Start Using UAL
Once enabled, you can begin searching audit logs:
- Go to: Microsoft Purview Portal
- Navigate to: Audit → Audit Search
- Use Filters to find activities like file access, mailbox actions, admin changes, etc.
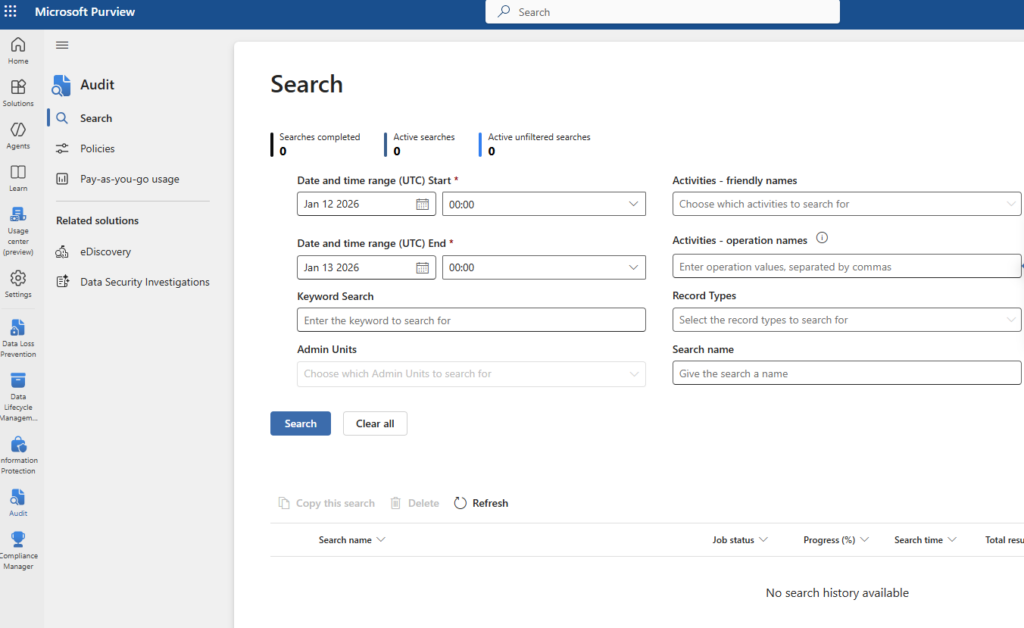
You can also configure Audit Policies, Alerts, and even integrate UAL logs into SIEM solutions for broader monitoring and automation.
Licensing Considerations
- Audit (Standard) is available with Microsoft 365 E3, Business Premium, and similar plans.
- Audit (Premium) — providing longer retention and more granular insights — requires Microsoft 365 E5, E5 Compliance, or an appropriate add-on license.
Be sure to check your tenant’s licensing to understand the level of auditing available.
Best Practices After Enabling UAL
- Set Appropriate Audit Retention Policies: Extend retention if you have compliance needs.
- Create Custom Alerts: Detect suspicious activities proactively.
- Export and Analyze Logs: Regularly review logs for trends and anomalies.
- Train Your Team: Ensure your security and compliance teams know how to use audit logs effectively.
- Integrate with Security Tools: Connect logs to Microsoft Sentinel or third-party SIEMs for broader security monitoring.